Podesta emails hack
Dems became the party of corruption: the organization did conspire against Sanders

Who are those "experts" who tell us those were Russians? Are those the same "experts"
who found weapons of mass destruction in Iraq? Or the same who claim that Hillary bathroom email server
was never breached?
“The same people on the Clinton team who made enormous efforts to claim her private
email server—which operated unencrypted over the Internet for three months, including during trips to
China and Russia, and which contained top-secret national-security data—was not hacked by the Russians
now are certain that the DNC server was hacked by the Russians”
http://www.theamericanconservative.com/articles/unpacking-the-dnc-emails/
Podesta essentially gave up his email due to committed by him blunder: sending his password to the
attacker. As such it was far from high-end hacking, which can be attributed to intelligence
agencies.
It is more like a regular, primitive phishing expedition
which became successful due to Podesta blunder. So this is not hacking but phishing
expedition... That makes big difference. He goa a face email from Google about changing his password.

This email was referred to Podesta ITt team, and one of his team members did not recognized that this is a spear fishing attempt, but
nevertheless send a sound advice:
This is a legitimate Email. John needs to change his password immediately,
and ensure that two-factor authentication is turned on his account.
He can go to this link: https://ayaccount.google.coa/security to do both.
It is absolutely imperative that this is done ASAP.
If you or he has any questions, please reach out to me
The key mistake was the phase "This is a legitimate Email." After that Podesta mistakenly clicked on initial links provided in the
email. That was a blunder that cost him a lot (although for perverts like Podesta this is some justice)
The fact that emails were downloaded to Wikileaks is of secondary importance. Emails depict dirty kitchen of closely link
Hillar campaign and DNC and attempt to sink Sanders, as well as a lot of other dirt.
Complete ignorance on the part of Podesta of elementary security protocols (never click on the link
in email is one of such rules; actually it should be disabled in his email reader) and incompetence of his staff (and Podesta himself) should be in the
center of the story. The person who was No.2 in the USA under Clinton (and in many areas probably No.1) can't afford a $25
hardware token for his email. You are kidding me...
That fact that nobody configured two factor authentication for his account in probably the most amazing part of this story.
This political genius Podesta looks like a complete idiot. His staff is no better.
Here is the defaulted story
How Podesta's
Gmail Account Was Breached The Smoking Gun

OCTOBER 28--So how did John Podesta’s e-mail account get hacked?
The answer to that question came into embarrassing focus this morning with the latest Wikileaks dump
of correspondence stolen from the Gmail account of Hillary Clinton’s
 campaign
chairman.
campaign
chairman.
On March 19, a Saturday, Podesta received
an e-mail--purportedly from Google--warning him that, “Someone has your password.” The alert (seen
above) informed Podesta that a sign-in attempt from an IP address in Ukraine was thwarted and that, “You
should change your password immediately.”
The e-mail, addressed "Hi John," included a blue “CHANGE PASSWORD” box to be clicked.
As TSG
reported in August, similar messages were sent to the Gmail accounts of scores of other Clinton
campaign officials around the time Podesta received the phony alert. An identical e-mail--containing the
exact Ukrainian IP address--was received on March 22 by William Rinehart, a campaign organizer. The IP
address included in the e-mails received by Podesta and Rinehart traces back to Kyivstar, Ukraine’s
largest telecommunications company.
Like Rinehart, Podesta’s Gmail account was compromised by the “spear phishing” e-mail, which American
investigators have concluded was
 the
work of Russian intelligence operatives.
the
work of Russian intelligence operatives.
After the e-mail arrived in Podesta’s account, it appears that his chief of staff, Sara Latham, sought
guidance from an IT worker with the Clinton campaign. After examining the “Someone has your password”
e-mail, staffer Charles Delavan (seen at left) mistakenly assured Latham and Shane Hable, the campaign’s
chief information officer, that, “This is a legitimate email. John needs to change his password
immediately, and ensure that two-factor authorization is turned on his account.”
Delavan’s 9:54 AM e-mail included a link to an actual Google password change page. “It is absolutely
imperative that this is done ASAP,” he added.
Latham then forwarded Delavan’s email to Podesta and campaign staffer Milia Fisher, who had access to
Podesta’s Gmail account. “The gmail one
 is
real,” wrote Latham, who instructed Fisher to change Podesta’s password since “Don’t want to lock him out
of his in box!”
is
real,” wrote Latham, who instructed Fisher to change Podesta’s password since “Don’t want to lock him out
of his in box!”
But instead of following the link provided by Delavan, it appears that Podesta or Fisher (pictured at
right) clicked on the “CHANGE PASSWORD” box in the original “spear phishing” correspondence (a copy of
which which was included in the e-mail chain
that Saturday morning).
That link led to what appeared to be a legitimate Google page, but was actually a site designed by the
hackers to capture a target’s log-in credentials. The link to the spoofed Gmail page included a lengthy
underlying url with the .tk suffix, indicating that the domain created to trick Podesta was registered in
Tokelau, a remote group of South Pacific atolls.
The hidden 293-character link included a string of characters containing the encoded Gmail address for
Podesta ([email protected]).
The e-mails stolen in the Podesta hack and posted on Wikileaks show that the most recent
correspondence is from March 21.
While Delavan protected his Twitter page following the
publication of this story, he did offer the public some sage advice earlier this week. In an
October 25 tweet, Delavan wrote, “don’t click on anything ever. delete your email account. move to
the woods.” (1 page)
- 20190421 : Escobar The Deep State Vs. WikiLeaks by Pepe Escobar ( Apr 20, 2019 , www.zerohedge.com )
- 20190404 : IRS warns of "Tax Transcript" email scam; dangers to business networks ( Apr 04, 2019 , www.irs.gov )
- 20190404 : How John Podesta's Emails Were Hacked And How To Prevent It From Happening To You ( Apr 04, 2019 , www.forbes.com )
- 20190404 : Don't Take the Bait, Step 1 Avoid Spear Phishing Emails ( Internal Revenue Service )
- 20190404 : Spear Phishing KnowBe4 ( Apr 04, 2019 , www.knowbe4.com )
- 20190404 : What is Spear-phishing Defining and Differentiating Spear-phishing from Phishing ( Digital Guardian )
- 20161106 : The Podesta Emails - Undeniable proof that the lobbyists wanted to put Bernie out ( Nov 06, 2016 , failedevolution.blogspot.gr )
- 20161104 : the Podesta emails show compete corruption of democratic party ( Nov 04, 2016 , www.theguardian.com )
- 20161103 : John Podesta and Mook conspiring to commit money laundering ( Nov 03, 2016 , www.nakedcapitalism.com )
- 20161103 : Off The Record dinner at Podestas with reporters covering Clinton ( Nov 03, 2016 , www.zerohedge.com )
- 20161030 : Speaking also of Pedesta email it is interesting that it was Podesta who make mistake of assessing phishing email link, probably accidentally ( turcopolier.typepad.com )
- 20161029 : Sometimes Bill And Hillary Have The Worst Judgment Wikileaks Releases Part 22 Of Podesta File ( Oct 29, 2016 , www.zerohedge.com )
- 20161026 : Over-sampling issue in Podesta emails ( crookedtimber.org )
- 20161019 : Wikileaks Releases Another 1803 Podesta Emails In Part 12 Of Data Dump; Total Is Now 18953 ( Oct 19, 2016 , www.zerohedge.com )
Notable quotes:
"... John Pilger, among few others, has already stressed how a plan to destroy WikiLeaks and Julian Assange was laid out as far back as 2008 – at the tail end of the Cheney regime – concocted by the Pentagon's shady Cyber Counter-Intelligence Assessments Branch. ..."
"... But it was only in 2017, in the Trump era, that the Deep State went totally ballistic; that's when WikiLeaks published the Vault 7 files – detailing the CIA's vast hacking/cyber espionage repertoire. ..."
"... This was the CIA as a Naked Emperor like never before – including the dodgy overseeing ops of the Center for Cyber Intelligence, an ultra-secret NSA counterpart. ..."
"... The monolithic narrative by the Deep State faction aligned with the Clinton machine was that "the Russians" hacked the DNC servers. Assange was always adamant; that was not the work of a state actor – and he could prove it technically. ..."
"... The DoJ wanted a deal – and they did make an offer to WikiLeaks. But then FBI director James Comey killed it. The question is why. ..."
"... Some theoretically sound reconstructions of Comey's move are available. But the key fact is Comey already knew – via his close connections to the top of the DNC – that this was not a hack; it was a leak. ..."
"... Ambassador Craig Murray has stressed, over and over again (see here ) how the DNC/Podesta files published by WikiLeaks came from two different US sources; one from within the DNC and the other from within US intel. ..."
"... he release by WikiLeaks in April 2017 of the malware mechanisms inbuilt in "Grasshopper" and the "Marble Framework" were indeed a bombshell. This is how the CIA inserts foreign language strings in source code to disguise them as originating from Russia, from Iran, or from China. The inestimable Ray McGovern, a VIPS member, stressed how Marble Framework "destroys this story about Russian hacking." ..."
"... No wonder then CIA director Mike Pompeo accused WikiLeaks of being a "non-state hostile intelligence agency" ..."
"... Joshua Schulte, the alleged leaker of Vault 7, has not faced a US court yet. There's no question he will be offered a deal by the USG if he aggress to testify against Julian Assange. ..."
"... George Galloway has a guest who explains it all https://www.youtube.com/watch?v=7VvPFMyPvHM&t=8s ..."
"... Escobar is brain dead if he can't figure out that Trumpenstein is totally on board with destroying Assange. As if bringing on pukes like PompAss, BoltON, and Abrams doesn't scream it. ..."
Authored by
Pepe Escobar via The Strategic Culture Foundation,
The Made-by-FBI indictment of
Julian Assange does look like a dead man walking. No evidence. No documents. No surefire
testimony. Just a crossfire of conditionals...
But never underestimate the legalese contortionism of US government (USG) functionaries. As
much as Assange may not be characterized as a journalist and publisher, the thrust of the
affidavit is to accuse him of conspiring to commit espionage.
In fact the charge is not even that Assange hacked a USG computer and obtained classified
information; it's that he may have discussed it with Chelsea Manning and may have had the
intention to go for a hack. Orwellian-style thought crime charges don't get any better than
that. Now the only thing missing is an AI software to detect them.
https://www.rt.com/shows/going-underground/456414-assange-wkileaks-asylum-london/video/5cb1c797dda4c822558b463f
Assange legal adviser Geoffrey Robertson – who also happens to represent another
stellar political prisoner, Brazil's Lula – cut
straight to the chase (at 19:22 minutes);
"The justice he is facing is justice, or injustice, in America I would hope the British
judges would have enough belief in freedom of information to throw out the extradition
request."
That's far from a done deal. Thus the inevitable consequence; Assange's legal team is
getting ready to prove, no holds barred, in a British court, that this USG indictment for
conspiracy to commit computer hacking is just an hors d'oeuvre for subsequent espionage
charges, in case Assange is extradited to US soil.
All about Vault 7
John Pilger, among few others, has already stressed how a plan to
destroy WikiLeaks and Julian Assange was laid out as far back as 2008 – at the tail end
of the Cheney regime – concocted by the Pentagon's shady Cyber Counter-Intelligence
Assessments Branch.
It was all about criminalizing WikiLeaks and personally smearing Assange, using "shock
troops enlisted in the media -- those who are meant to keep the record straight and tell us the
truth."
This plan remains more than active – considering how Assange's arrest has been covered
by the bulk of US/UK mainstream media.
By 2012, already in the Obama era, WikiLeaks detailed the astonishing "scale of the US Grand
Jury Investigation" of itself. The USG always denied such a grand jury existed.
"The US Government has stood up and coordinated a joint interagency criminal investigation
of Wikileaks comprised of a partnership between the Department of Defense (DOD) including:
CENTCOM; SOUTHCOM; the Defense Intelligence Agency (DIA); Defense Information Systems Agency
(DISA); Headquarters Department of the Army (HQDA); US Army Criminal Investigation Division
(CID) for USFI (US Forces Iraq) and 1st Armored Division (AD); US Army Computer Crimes
Investigative Unit (CCIU); 2nd Army (US Army Cyber Command); Within that or in addition,
three military intelligence investigations were conducted. Department of Justice (DOJ) Grand
Jury and the Federal Bureau of Investigation (FBI), Department of State (DOS) and Diplomatic
Security Service (DSS). In addition, Wikileaks has been investigated by the Office of the
Director of National Intelligence (ODNI), Office of the National CounterIntelligence
Executive (ONCIX), the Central Intelligence Agency (CIA); the House Oversight Committee; the
National Security Staff Interagency Committee, and the PIAB (President's Intelligence
Advisory Board)."
But it was only in 2017, in the Trump era, that the Deep State went totally ballistic;
that's when WikiLeaks published the Vault 7 files – detailing the CIA's vast
hacking/cyber espionage repertoire.
This was the CIA as a Naked Emperor like never before – including the dodgy
overseeing ops of the Center for Cyber Intelligence, an ultra-secret NSA counterpart.
WikiLeaks got Vault 7 in early 2017. At the time WikiLeaks had already published the DNC
files – which the unimpeachable Veteran Intelligence Professionals for Sanity (VIPS)
systematically proved was a leak, not a hack.
The monolithic narrative by the Deep State faction aligned with the Clinton machine was
that "the Russians" hacked the DNC servers. Assange was always adamant; that was not the work
of a state actor – and he could prove it technically.
There was some movement towards a deal, brokered by one of Assange's lawyers; WikiLeaks
would not publish the most damning Vault 7 information in exchange for Assange's safe passage
to be interviewed by the US Department of Justice (DoJ).
The DoJ wanted a deal – and they did make an offer to WikiLeaks. But then FBI
director James Comey killed it. The question is why.
It's a leak, not a hack
Some theoretically sound
reconstructions of Comey's move are available. But the key fact is Comey already knew
– via his close connections to the top of the DNC – that this was not a hack; it
was a leak.
Ambassador Craig Murray has stressed, over and over again (see
here ) how the DNC/Podesta files published by WikiLeaks came from two different US sources;
one from within the DNC and the other from within US intel.
There was nothing for Comey to "investigate". Or there would have, if Comey had ordered the
FBI to examine the DNC servers. So why talk to Julian Assange?
T he release by WikiLeaks in April 2017 of the malware mechanisms inbuilt in
"Grasshopper" and the "Marble Framework" were indeed a bombshell. This is how the CIA inserts
foreign language strings in source code to disguise them as originating from Russia, from Iran,
or from China. The inestimable Ray McGovern, a VIPS member, stressed how Marble Framework
"destroys this story about Russian hacking."
No wonder then CIA director Mike Pompeo accused WikiLeaks of being a "non-state hostile
intelligence agency", usually manipulated by Russia.
Joshua Schulte, the alleged leaker of Vault 7,
has not faced a US court yet. There's no question he will be offered a deal by the USG if he
aggress to testify against Julian Assange.
It's a long and winding road, to be traversed in at least two years, if Julian Assange is
ever to be extradited to the US. Two things for the moment are already crystal clear. The USG
is obsessed to shut down WikiLeaks once and for all. And because of that, Julian Assange will
never get a fair trial in the "so-called 'Espionage Court'" of the Eastern District of
Virginia, as
detailed by former CIA counterterrorism officer and whistleblower John Kiriakou.
Meanwhile, the non-stop demonization of Julian Assange will proceed unabated, faithful to
guidelines established over a decade ago. Assange is even accused of being a US intel op, and
WikiLeaks a splinter Deep State deep cover op.
Maybe President Trump will maneuver the hegemonic Deep State into having Assange testify
against the corruption of the DNC; or maybe Trump caved in completely to "hostile intelligence
agency" Pompeo and his CIA gang baying for blood. It's all ultra-high-stakes shadow play
– and the show has not even begun.
JailBanksters , 40 minutes ago
link
Not to mention the Pentagram has silenced 100,000 whistleblower complaints by
Intimidation, threats, money or accidents over 5 years . A Whistleblower only does this when
know there is something seriously wrong. Just Imagine how many knew something was wrong but
looked the other way.
ExPat2018 , 47 minutes ago
link
George Galloway has a guest who explains it all
https://www.youtube.com/watch?v=7VvPFMyPvHM&t=8s
Betrayed , 2 hours ago
link
Maybe President Trump will maneuver the hegemonic Deep State into having Assange testify
against the corruption of the DNC; or maybe Trump caved in completely to "hostile
intelligence agency" Pompeo and his CIA gang baying for blood.
Escobar is brain dead if he can't figure out that Trumpenstein is totally on board with
destroying Assange. As if bringing on pukes like PompAss, BoltON, and Abrams doesn't scream it.
besnook , 2 hours ago
link
assange and wikileaks are the real criminals despite being crimeless. the **** is a
sanctioned criminal, allowed to be criminal with the system because the rest of the
sanctioned criminals would be exposed if she was investigated.
this is not the rule of laws. this is the law of rulers.
_triplesix_ , 2 hours ago
link
Anyone seen Imran Awan lately?
Four chan , 34 minutes ago
link
yeah those ***** go free because they got everything on the stupid dems and they are
muslim.
assange exposes the podesta dws and clinton fraud against bernie voters+++ and hes the bad
guy. yeah right
hillary clinton murdered seth rich sure as **** too.
The IRS and Security Summit partners today warned the public of a surge of fraudulent emails
impersonating the IRS and using tax transcripts as bait to entice users to open documents
containing malware. See
IR-2018-226 .
Spear-phishing is a more sophisticated form of phishing that targets individuals using personally relevant
information. The spear-phasing email purports to come from a friend, a company you do business with such as your
bank, or an internet company you use like Google. The email will usually "inform" you that there is some problem or
issue that you need to clear up.
The email will also contain either a link or an attachment that allows the hacker access to your accounts. Opening
the attachment will typically deploy an exploit kit on your computer. Clicking the link will take you to a webpage
that spoofs the website of the company you think you're dealing with. The phony webpage will ask for the information
the hacker is trying to steal.
Nowadays most people reject simple phishing attacks as spam. Spear phishing is much more successful. The security
company
FireEye
reports that 70% of spear-phishing emails are opened by the recipient and 50% of the opened emails result
in the target clicking the link or opening the attachment. John Podesta was one of the people who clicked the link
Cybercriminals are endlessly creative. This year, some identity thieves hacked individuals'
emails accounts. Noticing that the individuals had been in email contact with tax preparers,
the criminals used the individual's email address to send a note to their preparer asking that
the direct deposit refund account number be changed. The scam prompted an IRS alert to
preparers about last-minute refund changes. See IR-2017-64
.
Protecting Your Clients and Your Business from Spear Phishing
There is no one action to protect your clients or your business from spear phishing. It
requires a series of defensive steps. Tax professionals should consider these basic steps:
- Educate all employees about phishing in general and spear phishing in particular.
- Use strong, unique passwords. Better yet, use a phrase instead of a word. Use different
passwords for each account. Use a mix of letters, numbers and special characters.
- Never take an email from a familiar source at face value; example: an email from "IRS
e-Services." If it asks you to open a link or attachment, or includes a threat to close your
account, think twice. Visit the
e-Services website for confirmation.
- If an email contains a link, hover your cursor over the link to see the web address (URL)
destination. If it's not a URL you recognize or if it's an abbreviated URL, don't open
it.
- Consider a verbal confirmation by phone if you receive an email from a new client sending
you tax information or a client requesting last-minute changes to their refund
destination.
- Use security software to help defend against malware, viruses and known phishing sites
and update the software automatically.
- Use the security options that come with your tax preparation software.
- Send suspicious tax-related phishing emails to [email protected] .
Malicious Attachments
Bad guys are exploiting a Microsoft vulnerability to bypass endpoint security software and
deliver the Remcos remote access Trojan via Microsoft PowerPoint decks.
The attack begins with spear phishing email, claiming to be from a cable manufacturing
provider and mainly targets organizations in the electronics manufacturing industry.
The sender's address is spoofed to look like a message from a business partner and the email
was written to look like an order request, with an attachment containing "shipping
information". Here is how it looks:
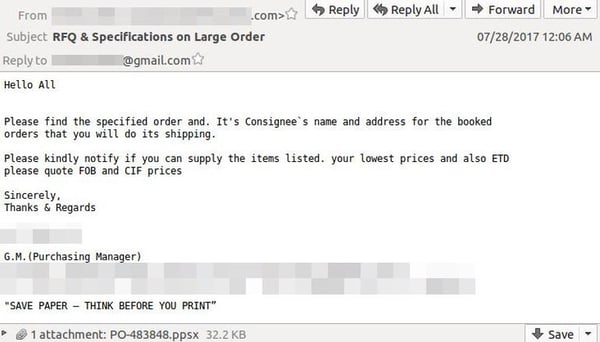
Once up and running on a system, Remcos allows keylogging, screenlogging, webcam and
microphone recorders, and the downloading and execution of additional malware. It can give the
attacker almost full control over the infected machine without the owner being
aware.
Ransomware Attacks
Many spear phishing attacks contain a ransomware payload. Defray ransomware is just one
example of a strain that targets healthcare, education, manufacturing and tech sectors in the
US and UK. The infection vector for Defray is spear phishing emails containing malicious
Microsoft Word document attachments, and the campaigns are as small as just a few messages
each.
Once opened, the attachment installs the ransomware. It has only been seen in small, very
targeted attacks and demands a high ransom of $5000. The image to the right is what the
document looks like.

Phishing vs Spear Phishing
While phishing and spear phishing attacks are similar, there are many key differences to be
aware of. A phishing campaign is very broad and automated, think 'spray and pray'. It doesn't
take a lot of skill to execute a massive phishing campaign. Most phishing attempts are after
things like credit card data, usernames and passwords, etc. and are usually a one-and-done
attack.
On the other hand, spear phishing is highly targeted, going after a specific employee,
company, or individuals within that company. This approach requires advanced hacking techniques
and a great amount of research on their targets. Spear phishers are after more valuable data
like confidential information, business secrets, and things of that nature. That is why a more
targeted approach is required; they find out who has the information they seek and go after
that particular person. A spear phishing email is really just the beginning of the attack as
the bad guys attempt to get access to the larger network.
Here's an infographic highlighting the
differences between phishing and spear phishing . 
Preventing Successful Spear Phishing Attacks
Now, how to mitigate against attacks like this? There is no single approach that will stop
this threat, but here is what you need to do to be a hard target for criminals:
- First of all, you need all your defense-in-depth layers in place.
Defending against attacks like this is a multi-layer approach. The trick is to make it as
hard as possible for the attacker to get through and to not rely on any single security
measure to keep your organization safe.
- Do not have a list of all email addresses of all employees on your website , use a web
form instead.
- Regularly scan the Internet for exposed email addresses and/or credentials, you would not
be the first one to find one of your user's username and password on a crime or porn
site.
- Never send out sensitive personal information via email . Be wary if you get an email
asking you for this info and when in doubt, go directly to the source.
- Enlighten your users about the dangers of oversharing their personal information on
social media sites . The more the bad guys know, the more convincing they can be when
crafting spear phishing emails.
- Users are your last line of defense! They need to be trained using new-school security
awareness training and receive frequent simulated phishing emails to keep them on their toes
with security top of mind. We provide the world's largest content library of security
awareness training combined with best in class pre- and post simulated phishing testing.
Since 91% of successful attacks use spear phishing to get in, this will get you by far the
highest ROI for your security budget, with visible proof the training
works!
.. and ALWAYS remember to Think Before You Click!
A definition of spear-phishing
Spear-phishing is a targeted attempt to steal sensitive information such as account
credentials or financial information from a specific victim, often for malicious reasons. This
is achieved by acquiring personal details on the victim such as their friends, hometown,
employer, locations they frequent, and what they have recently bought online. The attackers
then disguise themselves as a trustworthy friend or entity to acquire sensitive information,
typically through email or other online messaging. This is the most successful form of
acquiring confidential information on the internet, accounting for 91% of
attacks.
Spear-phishing vs. Phishing
Spear-phishing can easily be confused with phishing because they are both online attacks on
users that aim to acquire confidential information. Phishing is a broader term for any attempt
to trick victims into sharing sensitive information such as passwords, usernames, and credit
card details for malicious reasons. The attackers often disguise themselves as a trustworthy
entity and make contact with their target via email, social media, phone calls (often called
"vishing" for voice-phishing), and even text messages (often called "smishing" for
SMS-phishing).
Unlike spear-phishing attacks,
phishing attacks are not personalized to their victims, and are usually sent to masses of
people at the same time. The goal of phishing attacks is to send a spoofed email (or other
communication) that looks as if it is from an authentic organization to a large number of
people, banking on the chances that someone will click on that link and provide their personal
information or download malware. Spear-phishing attacks target a specific victim, and messages
are modified to specifically address that victim, purportedly coming from an entity that they
are familiar with and containing personal information. Spear-phishing requires more thought and
time to achieve than phishing. Spear-phishing attackers try to obtain as much personal
information about their victims as possible to make the emails that they send look legitimate
and to increase their chance of fooling recipients. Because of the personal level of these
emails, it is more difficult to identify spear-phishing attacks than to identify phishing
attacks conducted at a wide scale. This is why spear-phishing attacks are becoming more
prevalent.
How does spear-phishing work?
The act of spear-phishing may sound simple, but spear-phishing emails have improved within
the past few years and are now extremely difficult to detect without prior knowledge on
spear-phishing protection. Spear-phishing attackers target victims who put personal information
on the internet. They might view individual profiles while scanning a social networking site.
From a profile, they will be able to find a person's email address, friends list, geographic
location, and any posts about new gadgets that were recently purchased. With all of this
information, the attacker would be able to act as a friend or a familiar entity and send a
convincing but fraudulent message to their target.
To increase success rates, these messages often contain urgent explanations on why they need
sensitive information. Victims are asked to open a malicious attachment or click on a link that
takes them to a spoofed website where they are asked to provide passwords, account numbers,
PINs, and access codes. An attacker posing as a friend might ask for usernames and passwords
for various websites, such as Facebook, so that they would be able to access posted photos. In
reality, the attackers will use that password, or variations of it, to access different
websites that have confidential information such as credit card details or Social Security
Numbers. Once criminals have gathered enough sensitive information, they can access bank
accounts or even create a new identity using their victim's information. Spear-phishing can
also trick people into downloading malware or malicious codes after people click on links or
open attachments provided in messages.
6 tips to avoid a spear-phishing attack:
- Watch what personal information you post on the internet: Look at your online profiles.
How much personal information is available for potential attackers to view? If there is
anything that you do not want a potential scammer to see, do not post it – or at the
very minimum make sure that you've configured privacy settings to limit what others can
see.
- Have smart passwords: Do not just use one password or variations of passwords for every
account that you own. Reusing passwords or password variations means that if an attacker has
access to one of your passwords, they effectively have access to all of your accounts. Every
password that you have should be different from the rest – passwords with random
phrases, numbers, and letters are the most secure.
- Frequently update your software: If your software provider notifies you that there is a
new update, do it right away. The majority of software systems include security software
updates that should help to protect you from common attacks. Where possible, enable automatic
software updates.
- Do not click links in emails: If an organization, such as your bank, sends you a link,
launch your browser and go directly to the bank's site instead of clicking on the link
itself. You can also check the destination of a link by hovering your mouse over it. If the
URL does not match the link's anchor text or the email's stated destination, there is a good
chance that it could be malicious. Many spear-phishing attackers will try to obfuscate link
destinations by using anchor text that looks like a legitimate URL.
- Use logic when opening emails: If you get an email from a "friend" asking for personal
information including your password, carefully check to see if their email address is one
that you have seen them use in the past. Real businesses will not send you an email asking
for your username or password. Your best bet would be to contact that "friend" or business
outside of email, or visit the business' official website to see if they were the party who
actually contacted you.
- Implement a data protection program at your organization: A data protection program that
combines user education around data security best practices and implementation of a data
protection solution will help to prevent data loss due to spear-phishing attacks. For midsize
to larger corporations, data loss prevention software should
be installed to protect sensitive data from unauthorized access or egress, even if a user
falls for a phishing scam.
Tags: Data Protection 101
Notable quotes:
"... WikiLeaks series on deals involving Hillary Clinton campaign Chairman John Podesta. Mr Podesta is a long-term associate of
the Clintons and was President Bill Clinton's Chief of Staff from 1998 until 2001. Mr Podesta also owns the Podesta Group with his brother
Tony, a major lobbying firm and is the Chair of the Center for American Progress (CAP), a Washington DC-based think tank. ..."
"... if President Obama signs this terrible legislation that blatantly validates Bernie's entire campaign message about Wall Street
running our government, this will give Bernie a huge boost and 10,000 -20,000 outraged citizens (who WILL turn up because they will
be so angry at the President for preemption vt) will be marching on the Mall with Bernie as their keynote speaker. " ..."
"... But Hirshberg does not stop here. In order to persuade Podesta about the seriousness of the matter, he claims that " It will
be terrible to hand Sanders this advantage at such a fragile time when we really need to save our $$$ for the Trump fight. " ..."
WikiLeaks series on deals involving Hillary Clinton campaign Chairman John Podesta. Mr Podesta is a long-term associate of the
Clintons and was President Bill Clinton's Chief of Staff from 1998 until 2001. Mr Podesta also owns the Podesta Group with his brother
Tony, a major lobbying firm and is the Chair of the Center for American Progress (CAP), a Washington DC-based think tank.
An email from Gary Hirshberg, chairman and former
president and CEO of Stonyfield Farm , to John Podesta on March 13, 2016, confirms why the lobbyists strongly opposed
Bernie Sanders.
Hirshberg writes to a familiar person, as he was mentioned at the time as a possible 2008 Democratic candidate for the U.S. Senate,
requesting Obama should not pass the Roberts bill because " if President Obama signs this terrible legislation that blatantly
validates Bernie's entire campaign message about Wall Street running our government, this will give Bernie a huge boost and 10,000
-20,000 outraged citizens (who WILL turn up because they will be so angry at the President for preemption vt) will be marching on
the Mall with Bernie as their keynote speaker. "
But Hirshberg does not stop here. In order to persuade Podesta about the seriousness of the matter, he claims that " It will
be terrible to hand Sanders this advantage at such a fragile time when we really need to save our $$$ for the Trump fight. "
Notable quotes:
"... The emails currently roiling the US presidential campaign are part of some unknown digital collection amassed by the troublesome
Anthony Weiner, but if your purpose is to understand the clique of people who dominate Washington today, the emails that really matter
are the ones being slowly released by WikiLeaks from the hacked account of Hillary Clinton's campaign chair John Podesta. ..."
The emails currently roiling the US presidential campaign are part of some unknown digital collection amassed by the troublesome
Anthony Weiner, but if your purpose is to understand the clique of people who dominate Washington today, the emails that really matter
are the ones being slowly released by WikiLeaks from the hacked account of Hillary Clinton's campaign chair John Podesta. They
are last week's scandal in a year running over with scandals, but in truth their significance goes far beyond mere scandal: they
are a window into the soul of the Democratic party and into the dreams and thoughts of the class to whom the party answers.
The class to which I refer is not rising in angry protest; they are by and large pretty satisfied, pretty contented. Nobody takes
road trips to exotic West Virginia to see what the members of this class looks like or how they live; on the contrary, they are the
ones for whom such stories are written. This bunch doesn't have to make do with a comb-over TV mountebank for a leader; for this
class, the choices are always pretty good, and this year they happen to be excellent.
They are the comfortable and well-educated mainstay of our modern Democratic party. They are also the grandees of our national
media; the architects of our software; the designers of our streets; the high officials of our banking system; the authors of just
about every plan to fix social security or fine-tune the Middle East with precision droning. They are, they think, not a class at
all but rather the enlightened ones, the people who must be answered to but who need never explain themselves.
oho
November 3, 2016
at 3:03 pm
John Podesta + Mook conspiring to commit money laundering. Not hyperbole.
https://mobile.twitter.com/wikileaks/status/794236216681992192/photo/1
Portia
November 3, 2016
at 3:06 pm
3k/mo ok for you?
why yes
Notable quotes:
"... Hillary wouldn't even be close if the press weren't in the tank for her ..."
JackMeOff
Nov 3, 2016 9:37 AM
Off The Record dinner at Podesta's with reporters covering Clinton:
https://wikileaks.org/podesta-emails/emailid/43604
The goals of the dinner include:
(1) Getting to know the reporters most closely c overing HRC and getting them comfortable with team HRC
(2) Setting expectations for the announcement and launch period
(3) Framing the HRC message and framing the race
(4) Demystifying key players on HRC's campaign team
(5) Having fun and enjoying good cooking
I am a Man I am...
JackMeOff
Nov 3, 2016 10:01 AM ,
REPORTERS RSVP (28) 1. ABC – Liz Kreutz 2. AP – Julie Pace 3. AP - Ken Thomas 4. AP - Lisa Lerer 5. Bloomberg - Jennifer Epstein
6. Buzzfeed - Ruby Cramer 7. CBS – Steve Chagaris 8. CNBC - John Harwood 9. CNN - Dan Merica 10. Huffington Post - Amanda Terkel
11. LAT - Evan Handler 12. McClatchy - Anita Kumar 13. MSNBC - Alex Seitz-Wald 14. National Journal - Emily Schultheis 15. NBC
– Mark Murray 16. NPR - Mara Liassion 17. NPR – Tamara Keith 18. NYT - Amy Chozik 19. NYT - Maggie Haberman 20. Politico - Annie
Karni 21. Politico - Gabe Debenedetti 22. Politico - Glenn Thrush 23. Reuters - Amanda Becker 24. Washington Post - Anne Gearan
25. Washington Post – Phil Rucker 26. WSJ - Colleen McCain Nelson 27. WSJ - Laura Meckler 28. WSJ - Peter Nicholas
Pigeon •Nov 3, 2016 9:49 AM
It bothers me these stories are constantly prefaced with the idea that Wikileaks is saving Trump's bacon. Hillary wouldn't
even be close if the press weren't in the tank for her. How about Wikileaks evening the playing field with REAL STORIES AND
FACTS?
mistah charley, ph.d. said...
30 October 2016 at 09:13 AM
Speaking also of Podesta's email, not Huma's, the following is interesting:
http://www.cnn.com/2016/10/28/politics/phishing-email-hack-john-podesta-hillary-clinton-wikileaks/index.html
Briefly, it seems Podesta received an email "You need to change your password", asked for professional advice from his
staff if it was legit, was told "Yes, you DO need to change your password", but then clicked on the link in the original email,
which was sent him with malicious intent, as he suspected at first and then was inappropriately reassured about - rather than
on the link sent him by the IT staffer.
Result - the "phishing" email got his password info, and the world now gets to see all his emails.
Personally, my hope is that Huma and HRC will be pardoned for all their crimes, by Obama, before he leaves office.
Then I hope that Huma's divorce will go through, and that once Hillary is sworn in she will at last be courageous enough to
divorce Bill (who actually performed the Huma-Anthony Weiner nuptials - you don't have to make these things up).
Then it could happen that the first same-sex marriage will be performed in the White House, probably by the minister of DC's
Foundry United Methodist Church, which has a policy of LBGQT equality. Or maybe Hillary, cautious and middle-of-the-road as usual,
will go to Foundry UMC sanctuary for the ceremony, recognizing that some Americans' sensibilities would be offended by having
the rite in the White House.
As Nobel Laureate Bob Dylan wrote, "Love is all there is, it makes the world go round, love and only love, it can't be denied.
No matter what you think about it, you just can't live without it, take a tip from one who's tried."
Notable quotes:
"... and concludes by saying that " Sometimes HRC/WJC have the worst judgement ." In retrospect, she is right. ..."
In the aftermath of one of the most memorable (c)october shocks in presidential campaign history, Wikileaks continues its ongoing
broadside attack against the Clinton campaign with the relentless Podesta dump, by unveiling another 596 emails in the latest Part
22 of its Podesta release, bringing the total emails released so far to exactly 36,190, leaving less than 30% of the total dump left
to go.
RELEASE: The Podesta Emails Part 22 #PodestaEmails
#PodestaEmails22
#HillaryClinton
https://t.co/wzxeh70oUm
pic.twitter.com/QnWewcpPbf
- WikiLeaks (@wikileaks) October 29, 2016
As usual we will go parse through the disclosure and bring you some of the more notable ones.
* * *
In a February 2012 email from Chelsea Clinton's
NYU alias, [email protected] , to Podesta and Mills, Bill and Hillary's frustrated
daughter once again points out the "frustration and confusion" among Clinton Foundation clients in the aftermath of the previously
noted scandals plaguing the Clinton consultancy, Teneo:
Over the past few days a few people from the Foundation have reached out to me frustrated or upset about _____ (fill in the
blank largely derived meetings Friday or Monday). I've responded to all w/ essentially the following (ie disintermediating myself,
again, emphatically) below. I also called my Dad last night to tell him of my explicit non-involvement and pushing all back to
you both and to him as I think that is indeed the right answer. Thanks
Sample: Please share any and all concerns, with examples, without pulling punches, with John and Cheryl as appropriate and
also if you feel very strongly with my Dad directly. Transitions are always challenging and to get to the right answer its critical
that voices are heard and understood, and in the most direct way - ie to them without intermediation. Particularly in an effort
to move more toward a professionalism and efficiency at the Foundation and for my father - and they're the decision-makers, my
Dad most of all
* * *
A February 2015 email from Neera Tanden lashes
out at David Brock of the Bonner Group, profiled in this post: "
Money Laundering Scheme Exposed: 14 Pro-Clinton Super
PACs & Non-Profits Implicated ." As a reminder, the Bonner Group, as we showed last month, may be a money laundering front involving
various SuperPACs and non-profit institutions:
In the email Tanden says that:
"Brock/Bonner are a nightmare: Really, Suzie Buell isn't giving to the superpac? I wonder how that got in this story "
Big donors holding off making pledges to pro-Hillary Clinton super PAC ",
and concludes by saying that " Sometimes HRC/WJC have the worst judgement ." In retrospect, she is right.
* * *
Speaking of "donor advisor"
Mary Pat Bonner , the following email
from March 2009 hints at potential impropriety in shifting money from one
democratic donor group
to another, the
Center for
American Progress :
I have moved all the sussman money from unity '09 to cap and am reviewing the others . I will assess it and keep you informed
Something else for the DOJ to look into after the elections, perhaps?
* * *
And then there is this email from August 2015
in which German politician Michael Werz advises John Podesta that Turkish president Erdogan "is making substantial investments in
U.S. to counter opposition (CHP, Kurds, Gulenists etc.) outreach to policymakers" and the US Government.
John, heard this second hand but more than once. Seems Erdogan faction is making substantial investments in U.S. to counter
opposition (CHP, Kurds, Gulenists etc.) outreach to policymakers and USG. Am told that the Erdogan crew also tries to make inroads
via donations to Democratic candidates, including yours. Two names that you should be aware of are *Mehmet Celebi* and *Ali Cinar*.
Happy to elaborate on the phone, provided you are not shopping at the liquor store.
The email :
This should perhaps explain why the US has so far done absolutely nothing to halt Erdogan's unprecedented crackdown on "coup plotters"
which has seen as many as 100,000 workers lose their jobs, be arrested, or otherwise removed from Erdogan's political opposition.
Notable quotes:
"... The simplest explanation is usually best. All the indicators, especially the support of the donor class, elites of all kinds
etc. points towards a Democratic victory, perhaps a very strong victory if the poll numbers last weekend translate into electoral college
numbers. ..."
kidneystones 10.25.16 at 11:07 am (
55 )
I stopped by to check if my comment had cleared moderation. What follows is a more thorough examination (not my own, entirely)
on Corey's point 1, and some data that may point towards a much narrower race than we're led to believe.
The leaked emails from one Democratic super-pac, the over-sampling I cited at zerohedge (@13o) is part of a two-step process
involving over-sampling of Democrats in polls combined with high frequency polling. The point being to encourage media
to promote the idea that the race is already over. We saw quite a bit of this last weekend. Let's say the leaked emails are reliable.
This suggests to me two things: first – the obvious, the race is much closer than the polls indicated, certainly the poll cited
by Corey in the OP. Corey questioned the validity of this poll, at least obliquely. Second, at least one super-pac working with
the campaign sees the need to depress Trump turn-out. The first point is the clearest and the most important – the polls, some
at least, are intentionally tilted to support a 'Hillary wins easily' narrative. The second allows for some possibly useful speculation
regarding the Clinton campaigns confidence in their own GOTV success.
The simplest explanation is usually best. All the indicators, especially the support of the donor class, elites of all
kinds etc. points towards a Democratic victory, perhaps a very strong victory if the poll numbers last weekend translate into
electoral college numbers.
That's a big if. I suggest Hillary continues to lead but by much smaller margins in key states. It's also useful to
point out that Trump's support in traditionally GOP states may well be equally shaky.
And that really is it from me on this topic barring a double digit swing to Hillary in the LA Times poll that has the race
at dead even.
Layman 10.25.16 at 11:31 am
kidneystones:
"The leaked emails from one Democratic super-pac, the over-sampling I cited at zerohedge (@13o) is part of a two-step
process involving over-sampling of Democrats in polls combined with high frequency polling."
Excellent analysis, only the email in question is eight years old. And it refers to a request for internal polling done by
the campaign. And it suggests over-sampling of particular demographics so the campaign could better assess attitudes among those
demographics.
And this is a completely normal practice which has nothing to do with the polling carried out by independent third parties
(e.g. Gallup, Ipsos, etc) for the purposes of gauging and reporting to the public the state of the race.
And when pollsters to over-sample, the over-sampling is used for analysis but is not reflected in the top-line poll results.
Notable quotes:
"... Among the initial emails to stand out is this extensive exchange showing just how intimiately the narrative of Hillary's server
had been coached. The following September 2015 email exchange between Podesta and Nick Merrill, framed the "core language" to be used
in response to questions Clinton could be asked about her email server, and the decision to "bleach" emails from it. The emails contain
long and short versions of responses for Clinton. ..."
The daily dump continues. In the now traditional daily routine, one which forces the Clinton campaign to resort to ever more stark
sexual scandals involving Trump to provide a media distraction, moments ago Wikileaks released yet another 1,803 emails in Part 12
of its ongoing Podesta Email dump, which brings the total number of released emails to 18,953.
RELEASE: The Podesta Emails Part 12 https://t.co/wzxeh70oUm
#HillaryClinton
#imWithHer
#PodestaEmails
#PodestaEmails12
pic.twitter.com/druf7WQXD5
- WikiLeaks (@wikileaks) October 19, 2016
As a reminder among the most recent revelations we got further insights into Hillary's desire to see Obamacare "
unravel" , her contempt
for "doofus" Bernie Sanders, staff exchanges on handling media queries about Clinton "flip-flopping" on gay marriage, galvanizing
Latino support and locking down Clinton's healthcare policy. Just as notable has been the ongoing revelation of just how "captured"
the so-called independent press has been in its "off the record" discussions with John Podesta which got the head Politico correspondent,
Glenn Thrush, to admit he is a "hack" for allowing Podesta to dictate the content of his article.
The release comes on the day of the third and final presidential campaign between Hillary Clinton and Donald Trump, and as a result
we are confident it will be scrutinized especially carefully for any last minute clues that would allow Trump to lob a much needed
Hail Mary to boost his standing in the polls.
As there is a total of 50,000 emails, Wikileaks will keep the media busy over the next three weeks until the elections with another
30,000 emails still expected to be released.
* * *
Among the initial emails to stand out is this extensive exchange showing just how intimiately the narrative of Hillary's server
had been coached. The following September 2015 email
exchange between Podesta and Nick Merrill, framed the "core language" to be used in response to questions Clinton could be asked
about her email server, and the decision to "bleach" emails from it. The emails contain long and short versions of responses for
Clinton.
"Because the government already had everything that was work-related, and my personal emails were just that – personal – I
didn't see a reason to keep them so I asked that they be deleted, and that's what the company that managed my server did. And
we notified Congress of that back in March"
She was then presented with the following hypothetical scenario:
* "Why won't you say whether you wiped it?"
"After we went through the process to determine what was work related and what was not and provided the work related
emails to State, I decided not to keep the personal ones."
"We saved the work-related ones on a thumb drive that is now with the Department of Justice. And as I said in March, I chose
not to keep the personal ones. I asked that they be deleted, how that happened was up to the company that managed the server.
And they are cooperating fully with anyone that has questions."
* * *
Another notable email reveals the close
relationship between the Clinton Foundation and Ukraine billionaire Victor Pinchuk, a
prominent
donor to the Clinton Foundation , in which we see the latter's attempt to get a meeting with Bill Clinton to show support for
Ukraine:
From: Tina Flournoy < [email protected] >
Sent: Monday, March 30, 2015 9:58:55 AM
To: Amitabh Desai
Cc: Jon Davidson; Margaret Steenburg; Jake Sullivan; Dan Schwerin; Huma Abedin; John Podesta
Subject: Re: Victor Pinchuk
Team HRC - we'll get back to you on this
> On Mar 30, 2015, at 9:53 AM, Amitabh Desai < [email protected] > wrote:
>
> Victor Pinchuk is relentlessly following up (including this morning) about a meeting with WJC in London or anywhere in Europe.
Ideally he wants to bring together a few western leaders to show support for Ukraine, with WJC probably their most important participant.
If that's not palatable for us, then he'd like a bilat with WJC.
>
> If it's not next week, that's fine, but he wants a date. I keep saying we have no Europe plans, although we do have those events
in London in June. Are folks comfortable offering Victor a private meeting on one of those dates? At this point I get
the impression that although I keep saying WJC cares about Ukraine, Pinchuk feels like WJC hasn't taken enough action to demonstrate
that, particularly during this existential moment for the county and for him.
>
> I sense this is so important because Pinchuk is under Putin's heel right now, feeling a great degree of pressure and pain for
his many years of nurturing stronger ties with the West.
>
> I get all the downsides and share the concerns. I am happy to go back and say no. It would just be good to
know what WJC (and HRC and you all) would like to do, because this will likely impact the future of this relationship, and slow
walking our reply will only reinforce his growing angst.
>
> Thanks, and sorry for the glum note on a Monday morning...
* * *
We find more evidence of media coordination with
Politico's Glenn Thrush who has an off the record question to make sure he is not "fucking anything up":
From: [email protected]
To: [email protected]
Date: 2015-04-30 17:06
Subject: Re: sorry to bother...
Sure. Sorry for the delay I was on a plane.
On Apr 30, 2015 9:44 AM, "Glenn Thrush" < [email protected]
> wrote:
> Can I send u a couple of grafs, OTR, to make sure I'm not fucking
> anything up?
* * *
Another notable moment emerges in the emails, involving Hillary Clinton's selective memory. Clinton's description of herself as
a moderate Democrat at a September 2015 event in Ohio caused an uproar amongst her team. In a
mail from Clinton advisor Neera Tanden to Podesta
in the days following the comment she asks why she said this.
"I pushed her on this on Sunday night. She claims she didn't remember saying it. Not sure I believe her," Podesta replies.
Tanden insists that the comment has made her job more difficult after "telling every reporter I know she's actually progressive".
" It worries me more that she doesn't seem to know what planet we are all living in at the moment ," she adds.
* * *
We also get additional insight into Clinton courting the Latino minority. A November 2008
email from Federico Peńa , who was on the Obama-Biden
transition team, called for a "Latino media person" to be added to the list of staff to appeal to Latino voters. Federico de Jesus
or Vince Casillas are seen as ideal candidates, both of whom were working in the Chicago operations.
"More importantly, it would helpful (sic) to Barack to do pro-active outreach to Latino media across the country to get our
positive message out before people start spreading negative rumors," Peńa writes.
* * *
Another email between Clinton's foreign policy adviser
Jake Sullivan and Tanden from March 2016 discussed how it was "REALLY dicey territory" for Clinton to comment on strengthening
"bribery laws to ensure that politicians don't change legislation for political donations." Tanden agrees with Sullivan:
" She may be so tainted she's really vulnerable - if so, maybe a message of I've seen how this sausage is
made, it needs to stop, I'm going to stop it will actually work."
* * *
One email suggested, sarcastically, to kneecap
bernie Sanders : Clinton's team issued advise regarding her tactics for the "make or break" Democratic presidential debate with
Sanders in Milwaukee on February 11, 2016. The mail to Podesta came from Philip Munger, a Democratic Party donor. He sent the mail
using an encrypted anonymous email service.
"She's going to have to kneecap him. She is going to have to take him down from his morally superior perch. She has done so
tentatively. She must go further," he says.
Clearly, the desire to get Sanders' supporters was a key imperative for the Clinton campaign. In a
September 2015 email to Podesta , Hill columnist
Brent Budowsky criticized the campaign for allegedly giving Clinton surrogates talking points to attack Bernie Sanders. "I cannot
think of anything more stupid and self-destructive for a campaign to do," he says. "Especially for a candidate who has dangerously
low levels of public trust," and in light of Sanders' campaign being based on "cleaning up politics."
Budowsky warns voters would be "disgusted" by attacks against Sanders and says he wouldn't discourage Podesta from sharing the
note with Clinton because "if she wants to become president she needs to understand the point I am making with crystal clarity."
"Make love to Bernie and his idealistic supporters, and co-opt as many of his progressive issues as possible."
Budowsky then adds that he was at a Washington university where " not one student gave enough of a damn for Hillary to
open a booth, or even wear a Hillary button. "
* * *
One email focused on how to address with the
topic of the TPP. National Policy Director for Hillary for America Amanda Renteria explains, "The goal here was to minimize our vulnerability
to the authenticity attack and not piss off the WH any more than necessary."
Democratic pollster Joel Benenson says, "the reality is HRC is more pro trade than anti and trying to turn her into something
she is not could reinforce our negative [sic] around authenticity. This is an agreement that she pushed for and largely advocated
for."
* * *
While claiming she is part of the people, an email exposes Hillary as being "
part of the system ." Clinton's team acknowledges
she is "part of the system" in an email regarding her strategies. As Stan Greenberg told Podesta:
" We are also going to test some messages that include acknowledgement of being part of the system, and know how much
has to change ,"
* * *
Some more on the topic of Hillary being extensively coached and all her words rehearsed, we find an email which reveals that
Clinton's words have to be tightly managed by her
team who are wary of what she might say. After the Iowa Democratic Party's presidential debate in November 2015 adviser Ron Klain
mails Podesta to say, "If she says something three times as an aside during practice (Wall Street supports me due to 9/11), we need
to assume she will say it in the debate, and tell her not to do so." Klain's mail reveals Sanders was their biggest fear in the debate.
"The only thing that would have been awful – a Sanders break out – didn't happen. So all in all, we were fine," he says.
The mail also reveals Klain's role in securing his daughter Hannah a position on Clinton's team. "I'm not asking anyone to make
a job, or put her in some place where she isn't wanted – it just needs a nudge over the finish line," Klain says. Hannah Klain worked
on Clinton's Surrogates team for nine months commencing in the month after her father's mail to Podesta, according to her Linkedin.
CuttingEdge
X_in_Sweden
Oct 19, 2016 9:18 AM
Is Podesta authorised to be privy to confidential information?
Only Hillary sends him a 9-point assessment of the ME with this at the top:
Note: Sources include Western intelligence, US intelligence and sources in the region.
I would assume Intelligence Services intel based assessments would be a bit confidential, Mr Comey? Given their source? Nothing
to see here, you say?
Fuck Me.
https://www.wikileaks.org/podesta-emails/emailid/18917
Bubba Rum Das
samjam7
Oct 19, 2016 9:02 AM
I love this...Assange is incommunicado, yet the data dumps keep coming!
Horse face looks like such a fool to the world as a result; & due to John Kerry's stupidity which is drawing major attention to
the whole matter; Americans are finally beginning to wake up & pay attention to this shit!
Looks like the Hitlery for Prez ship is starting to take on MASSIVE amounts of water!
I believe they are beyond the point where any more news of 'pussy grabbing' will save them from themselves (and Mr. Assange)!
Oh, yeah...-And THANK YOU, MR. O'KEEFE!
css1971
Oct 19, 2016 9:04 AM
Dems!! Dems!! Where are you. You need 2 more bimbos to accuse Trump of looking at them!!
- You have more paedophile charges to lay on Assange.
- You have violence to cause at Trump, Stein and Johnson rallys.
- You have mass vote rigging campaigns to orchestrate!!!
DEMS you need to get that nose to the grindstone!!
Hobbleknee
GunnerySgtHartman
Oct 19, 2016 8:48 AM
Fox is controlled opposition. They dropped the interview with O'Keefe after he released the latest undercover report on Democrat
voter fraud.
JackMeOff
Oct 19, 2016 10:16 AM
Wonder what "docs" they are referring?
https://wikileaks.org/podesta-emails/emailid/17978
monad
Oct 19, 2016 1:14 PM The FBI had no difficulty convicting Obugger's crony Rod Blagegovitch.
The new lowered expectations federal government just expects to get lucre + bennies for sitting on their asses and holding
the door for gangsters. Traitors. Spies. Enemies foreign and domestic. Amphisbaegenic pot boiling.
california chrome
Oct 19, 2016 11:03 AM
With Creamer's tricks effective in Obama's re-election, it now makes sense why Obama was so confident when he said Trump would
never be president.
Trump is still ahead in the only poll I track. But i conduct my own personal poll on a daily basis and loads of Trump supporters
are in the closet and won't come out until they pull the lever for Trump on election day.
http://graphics.latimes.com/usc-presidential-poll-dashboard/
whatamaroon
Oct 19, 2016 1:04 PM https://pageshot.net/qLjtSLje2gBJ1Mlp/twitter.com
,
This supposedly directly implicates Podesta and voter fraud. If it will open here
Softpanorama Recommended
WikiLeaks - Search the DNC email database
How John Podesta's emails were hacked - YouTube
How Podesta's Gmail Account Was
Breached The Smoking Gun
Society
Groupthink :
Two Party System
as Polyarchy :
Corruption of Regulators :
Bureaucracies :
Understanding Micromanagers
and Control Freaks : Toxic Managers :
Harvard Mafia :
Diplomatic Communication
: Surviving a Bad Performance
Review : Insufficient Retirement Funds as
Immanent Problem of Neoliberal Regime : PseudoScience :
Who Rules America :
Neoliberalism
: The Iron
Law of Oligarchy :
Libertarian Philosophy
Quotes
War and Peace
: Skeptical
Finance : John
Kenneth Galbraith :Talleyrand :
Oscar Wilde :
Otto Von Bismarck :
Keynes :
George Carlin :
Skeptics :
Propaganda : SE
quotes : Language Design and Programming Quotes :
Random IT-related quotes :
Somerset Maugham :
Marcus Aurelius :
Kurt Vonnegut :
Eric Hoffer :
Winston Churchill :
Napoleon Bonaparte :
Ambrose Bierce :
Bernard Shaw :
Mark Twain Quotes
Bulletin:
Vol 25, No.12 (December, 2013) Rational Fools vs. Efficient Crooks The efficient
markets hypothesis :
Political Skeptic Bulletin, 2013 :
Unemployment Bulletin, 2010 :
Vol 23, No.10
(October, 2011) An observation about corporate security departments :
Slightly Skeptical Euromaydan Chronicles, June 2014 :
Greenspan legacy bulletin, 2008 :
Vol 25, No.10 (October, 2013) Cryptolocker Trojan
(Win32/Crilock.A) :
Vol 25, No.08 (August, 2013) Cloud providers
as intelligence collection hubs :
Financial Humor Bulletin, 2010 :
Inequality Bulletin, 2009 :
Financial Humor Bulletin, 2008 :
Copyleft Problems
Bulletin, 2004 :
Financial Humor Bulletin, 2011 :
Energy Bulletin, 2010 :
Malware Protection Bulletin, 2010 : Vol 26,
No.1 (January, 2013) Object-Oriented Cult :
Political Skeptic Bulletin, 2011 :
Vol 23, No.11 (November, 2011) Softpanorama classification
of sysadmin horror stories : Vol 25, No.05
(May, 2013) Corporate bullshit as a communication method :
Vol 25, No.06 (June, 2013) A Note on the Relationship of Brooks Law and Conway Law
History:
Fifty glorious years (1950-2000):
the triumph of the US computer engineering :
Donald Knuth : TAoCP
and its Influence of Computer Science : Richard Stallman
: Linus Torvalds :
Larry Wall :
John K. Ousterhout :
CTSS : Multix OS Unix
History : Unix shell history :
VI editor :
History of pipes concept :
Solaris : MS DOS
: Programming Languages History :
PL/1 : Simula 67 :
C :
History of GCC development :
Scripting Languages :
Perl history :
OS History : Mail :
DNS : SSH
: CPU Instruction Sets :
SPARC systems 1987-2006 :
Norton Commander :
Norton Utilities :
Norton Ghost :
Frontpage history :
Malware Defense History :
GNU Screen :
OSS early history
Classic books:
The Peter
Principle : Parkinson
Law : 1984 :
The Mythical Man-Month :
How to Solve It by George Polya :
The Art of Computer Programming :
The Elements of Programming Style :
The Unix Hater’s Handbook :
The Jargon file :
The True Believer :
Programming Pearls :
The Good Soldier Svejk :
The Power Elite
Most popular humor pages:
Manifest of the Softpanorama IT Slacker Society :
Ten Commandments
of the IT Slackers Society : Computer Humor Collection
: BSD Logo Story :
The Cuckoo's Egg :
IT Slang : C++ Humor
: ARE YOU A BBS ADDICT? :
The Perl Purity Test :
Object oriented programmers of all nations
: Financial Humor :
Financial Humor Bulletin,
2008 : Financial
Humor Bulletin, 2010 : The Most Comprehensive Collection of Editor-related
Humor : Programming Language Humor :
Goldman Sachs related humor :
Greenspan humor : C Humor :
Scripting Humor :
Real Programmers Humor :
Web Humor : GPL-related Humor
: OFM Humor :
Politically Incorrect Humor :
IDS Humor :
"Linux Sucks" Humor : Russian
Musical Humor : Best Russian Programmer
Humor : Microsoft plans to buy Catholic Church
: Richard Stallman Related Humor :
Admin Humor : Perl-related
Humor : Linus Torvalds Related
humor : PseudoScience Related Humor :
Networking Humor :
Shell Humor :
Financial Humor Bulletin,
2011 : Financial
Humor Bulletin, 2012 :
Financial Humor Bulletin,
2013 : Java Humor : Software
Engineering Humor : Sun Solaris Related Humor :
Education Humor : IBM
Humor : Assembler-related Humor :
VIM Humor : Computer
Viruses Humor : Bright tomorrow is rescheduled
to a day after tomorrow : Classic Computer
Humor
The Last but not Least Technology is dominated by
two types of people: those who understand what they do not manage and those who manage what they do not understand ~Archibald Putt.
Ph.D
Copyright © 1996-2021 by Softpanorama Society. www.softpanorama.org
was initially created as a service to the (now defunct) UN Sustainable Development Networking Programme (SDNP)
without any remuneration. This document is an industrial compilation designed and created exclusively
for educational use and is distributed under the Softpanorama Content License.
Original materials copyright belong
to respective owners. Quotes are made for educational purposes only
in compliance with the fair use doctrine.
FAIR USE NOTICE This site contains
copyrighted material the use of which has not always been specifically
authorized by the copyright owner. We are making such material available
to advance understanding of computer science, IT technology, economic, scientific, and social
issues. We believe this constitutes a 'fair use' of any such
copyrighted material as provided by section 107 of the US Copyright Law according to which
such material can be distributed without profit exclusively for research and educational purposes.
This is a Spartan WHYFF (We Help You For Free)
site written by people for whom English is not a native language. Grammar and spelling errors should
be expected. The site contain some broken links as it develops like a living tree...
Disclaimer:
The statements, views and opinions presented on this web page are those of the author (or
referenced source) and are
not endorsed by, nor do they necessarily reflect, the opinions of the Softpanorama society. We do not warrant the correctness
of the information provided or its fitness for any purpose. The site uses AdSense so you need to be aware of Google privacy policy. You you do not want to be
tracked by Google please disable Javascript for this site. This site is perfectly usable without
Javascript.
Last modified: March, 12, 2020
![]()
 campaign
chairman.
campaign
chairman. the
work of Russian intelligence operatives.
the
work of Russian intelligence operatives. is
real,” wrote Latham, who instructed Fisher to change Podesta’s password since “Don’t want to lock him out
of his in box!”
is
real,” wrote Latham, who instructed Fisher to change Podesta’s password since “Don’t want to lock him out
of his in box!”



